Vulnerabilities in systems, processes, and human behavior can be exploited, leading to financial loss, reputational damage, and regulatory consequences. Effective risk management strategies are crucial for safeguarding assets, maintaining trust, and ensuring long-term operational resilience.
Cybersecurity incidents, ranging from ransomware attacks to insider breaches, have become more sophisticated and frequent. Operational risks, such as supply chain disruptions or equipment failures, can compound the effects of cyber threats and strain resources. Organizations must adopt a comprehensive approach that addresses both technological and procedural vulnerabilities to maintain performance and reliability.

Identifying and Understanding Risks
The first step in risk management is identifying potential vulnerabilities across systems, processes, and personnel. Cyber risks include malware, phishing, and unauthorized access, while operational risks may involve equipment failure, human error, or regulatory non-compliance. Thorough analysis ensures that mitigation efforts target the most critical areas.
Organizations can perform risk assessments, internal audits, and scenario planning to anticipate threats. Evaluating the likelihood and impact of each risk helps prioritize resources effectively. Understanding the scope of risks enables informed decision-making and strategic planning.
Monitoring trends and emerging threats is vital for maintaining situational awareness. Cybercriminals continuously develop new techniques, while operational challenges evolve with technology and market conditions. Staying informed allows businesses to adapt quickly and maintain resilience.
Strengthening Data Protection and Cybersecurity
Protecting sensitive data is a central component of risk management. Encryption, secure authentication, and network monitoring safeguard information from unauthorized access. Businesses must adopt solutions that address current vulnerabilities while preparing for future threats.
Emerging quantum computing capabilities necessitate forward-looking security measures. Organizations should consider implementing quantum safe encryption in cryptography to protect critical information against next-generation cyber attacks. Advanced cryptographic techniques provide long-term security for sensitive data and operational continuity.
Regularly updating security protocols, performing vulnerability scans, and training staff ensures a robust defense. Combining technical measures with human vigilance strengthens protection. Businesses that prioritize cybersecurity can reduce risk exposure significantly.
Building a Multi-Layered Defense Strategy
No single measure can fully prevent cyber or operational risks. A multi-layered defense incorporates firewalls, intrusion detection systems, access controls, and employee training. Each layer addresses different vulnerabilities and creates redundancy for enhanced protection.
Organizational culture plays a key role in defense strategy. Staff awareness and compliance with protocols reduce the likelihood of breaches and operational errors. Periodic audits and drills reinforce proper procedures and highlight areas for improvement.
Continuous testing ensures that each layer functions as intended. Penetration tests, scenario simulations, and response exercises validate system effectiveness. A layered approach provides flexibility and resilience against evolving threats.
Ensuring Regulatory Compliance
Adherence to industry regulations protects businesses from legal penalties and reputational damage. Compliance frameworks, such as GDPR, HIPAA, or industry-specific standards, require secure handling of data and operational accountability. Meeting these requirements demonstrates due diligence and builds stakeholder trust.
Organizations must integrate compliance into daily operations. Regular audits, policy reviews, and documentation verify adherence and highlight areas for improvement. Proactive compliance measures prevent violations before they occur and support continuous operational integrity.
Embedding regulatory compliance within risk management ensures that legal obligations are consistently met. Employees are trained to follow protocols, and technological tools enforce standards. This integrated approach reinforces both security and accountability.
Employee Training and Awareness
Human factors are a leading cause of cyber and operational incidents. Employees must be trained to recognize threats, follow security protocols, and respond to incidents appropriately. Continuous education fosters a culture of vigilance and responsibility.
Simulation exercises, phishing tests, and scenario-based training improve preparedness. Staff members become adept at identifying suspicious activity and mitigating potential risks. Engagement and reinforcement strengthen organizational defenses across all levels.
Leaders must model and support proper risk management behavior. Policies should be clear, communicated regularly, and enforced consistently. Empowered employees enhance the security and operational resilience of the organization.
Developing an Incident Response Plan
Even with robust prevention measures, breaches and operational failures may still occur. A structured incident response plan enables quick detection, containment, and recovery. Well-prepared organizations reduce downtime, financial losses, and reputational harm.
Plans should define roles, responsibilities, and communication protocols. Regular testing, simulations, and scenario exercises ensure that teams are ready to act effectively. Continuous improvement based on past incidents strengthens resilience and response capabilities.
Key incident response steps:
- Detection and categorization of incidents
- Immediate containment and mitigation measures
- Recovery of systems and data
- Post-incident review to enhance future preparedness
An organized response minimizes impact and accelerates operational restoration.
Leveraging Technology for Risk Management
Advanced technologies enhance both cybersecurity and operational risk management. Artificial intelligence, predictive analytics, and monitoring tools identify anomalies, anticipate threats, and optimize responses. Automation reduces human error and supports real-time decision-making.
Selecting the right tools requires analysis of organizational needs, system compatibility, and scalability. Implementing software solutions, secure communication platforms, and monitoring frameworks strengthens security. Integrating technology with human oversight ensures balanced, effective risk management.
Regular updates, patching, and performance monitoring maintain system integrity. Technology evolves rapidly, and businesses must adapt to emerging solutions. Combining advanced tools with strategic planning enhances both efficiency and security.
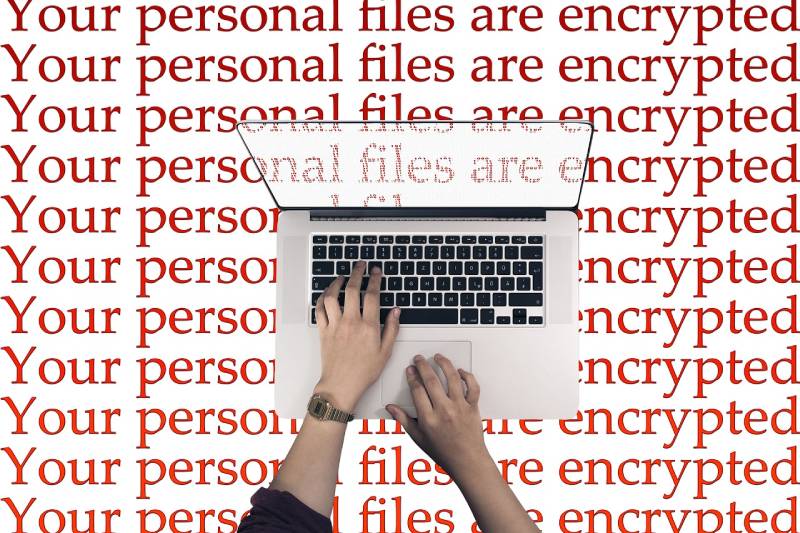
Managing cyber and operational risks is important for sustaining business continuity, protecting assets, and maintaining trust. A combination of proactive planning, layered defenses, and employee engagement reduces vulnerabilities and enhances resilience. Implementing advanced encryption, operational safeguards, and regulatory compliance strengthens risk management.
Forward-looking organizations adopt quantum-safe encryption in cryptography to future-proof critical information against emerging threats. Integrating technology, culture, and strategy ensures comprehensive protection. Businesses that prioritize risk management remain agile, secure, and competitive in complex environments.